Are you drowning in spreadsheets?
Kordon’s GRC platform saves you hours, reduces audit times by 80%, and keeps your team aligned.
Spreadsheets weren’t built for GRC—Kordon is.
Trusted by
and many more
Spreadsheets are great, until they're not
Audits take too much time
No Big Picture
Always in Follow-up Mode
Experience the Kordon GRC platform Advantage
With Kordon GRC platform, you're not just ticking boxes—you're building a robust security program with daily visibility into where your company stands.
Goodbye Excel chaos
Centralise your entire security program in one intuitive platform, eliminating the need for scattered spreadsheets and last-minute scramble.
Big picture
Get real-time insight into how your security program covers framework requirements and discover the next most impactful action to strengthen your security posture.
Focus on actual security, not busywork
Free up your team's time to concentrate on strategic improvements rather than administrative tasks.
Time-saving automation
Reduce compliance workload by up to 80% through evidence collection and task automation.
Faster audits
As read only users, auditors can get everything they need from the app. No more sending documents back and forth.
Proactive compliance
Shift from reactive audit preparation to continuous compliance, with automated collection of evidence.
Packed with Features
Control Management
Work with the controls you already have in place or use Kordon's templates as starting point. Connect controls with requiermens from one or multiple frameworks and reduce duplication of effort.
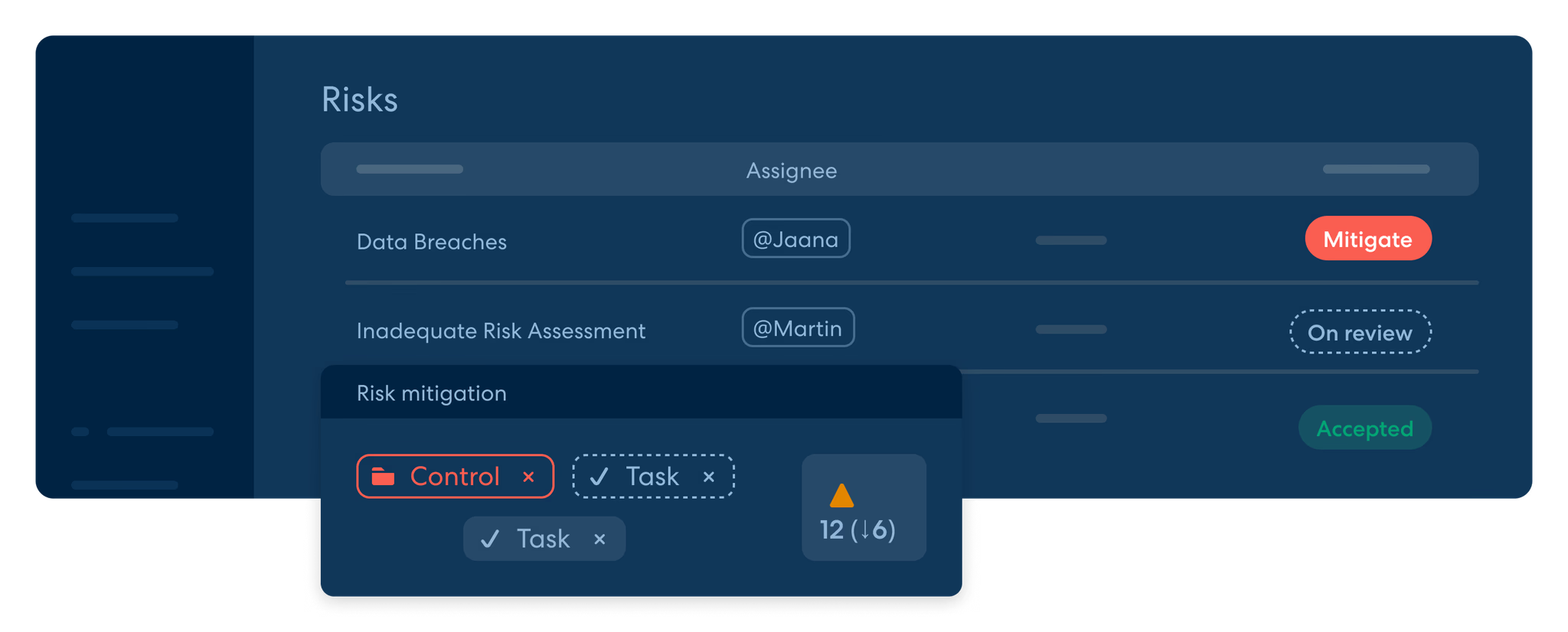
Risk Management
Go beyond just documenting risks and gain live insight into how well your risk management and controls are working. Risk management in Kordon links risks to dynamic controls to effectively monitor and reduce threats.
Risk Management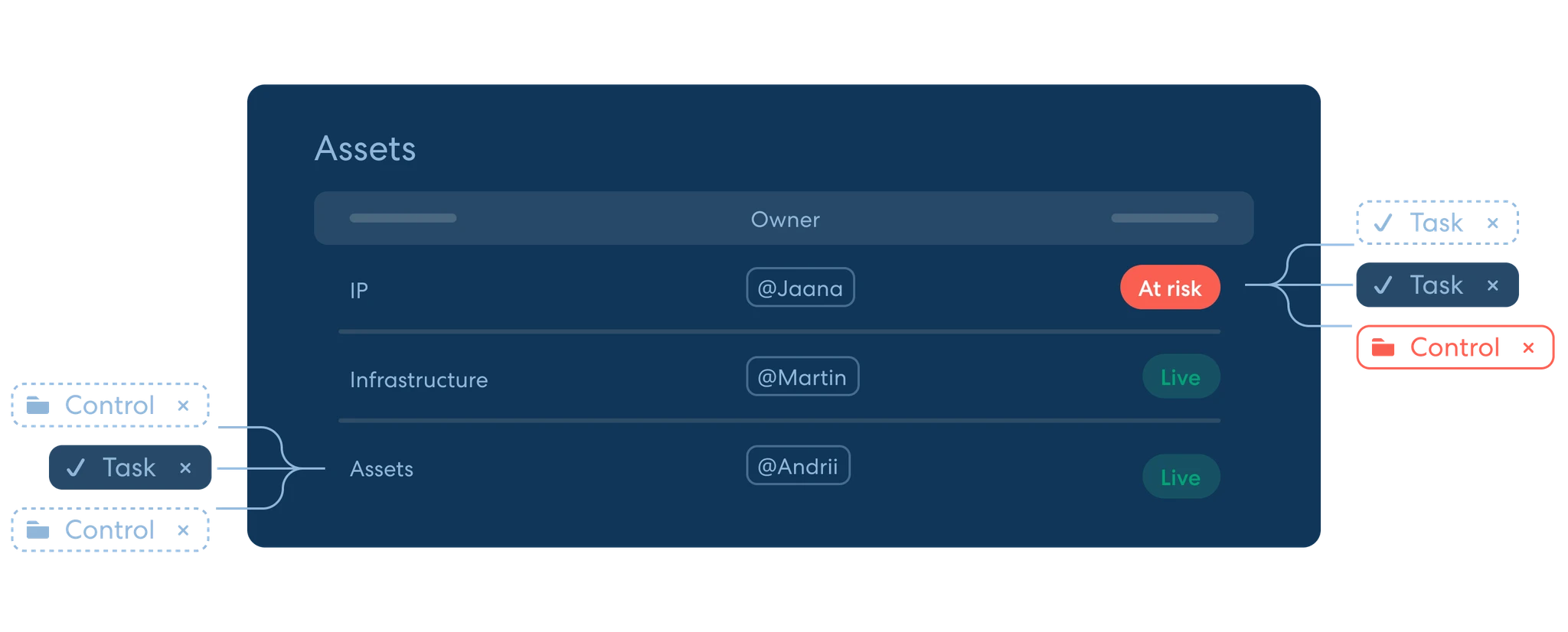
Asset Management
Connect assets to both dynamic controls and associated risks to manage, monitor and protect your assets based on the actual effectiveness of your security measures.
Asset Management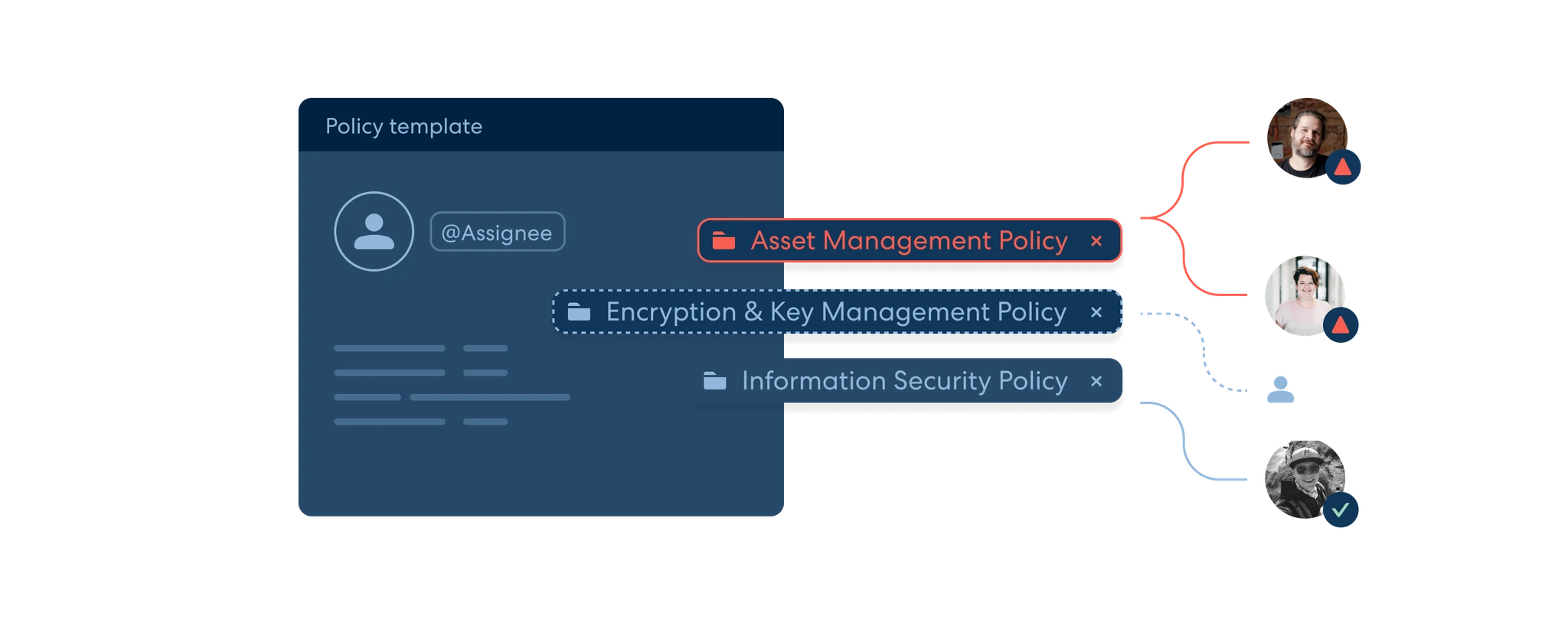
Policy Management
Take control over your policy process from drafting and reviewing to employee acceptance. Start with one of our 20+ policy templates or bring your own.
Policy ManagementAutomated Evidence Collection
Reduce compliance workload by up to 80% through automated task assignments and reminders.
Powerful API
Extend the capabilities of Kordon using the powerful API. Automate workflows further by integrating Kordon with your other systems.
Advanced Permissions
With our flexible visibility and permission system, everyone can see and do exactly what they need, not more, not less.
Works with hundreds of Frameworks
Kordon GRC platform works with any and all information security, quality, environmental, health & safety, food safety, data privacy, and risk management frameworks.





and many more
What People Say About Working With Us

Karl Leppmets
Internal IT and IT Security Manager at Scoro
"Kordon has streamlined our security program management, making it easier than ever. From day one, Kordon helped us identify and address gaps in our controls."

Urmo Laaneots
Chief Information Security Officer at e-Governance Academy
"Kordon has been a game changer for us, combining ISO 9001 and ISO 27001 in one system. It’s streamlined compliance and boosted risk management, helping us identify and address risks more effectively and adding real value to our security and quality processes."