09 May

Fourth week in a row, I spent hours going throguh 20+ different cyber security news sources to find most interesting articles from last week so you can quickly catch up on only the most interesting cyber news quickly.
1. Germany Most Targeted Country in Q1 2025 DDoS Attacks
Summary DDoS attacks surged 358% year-over-year in early 2025, with Germany facing the brunt of global activity. While attackers increasingly rely on short, high-volume bursts to overwhelm systems, many organizations still lack the automated defenses needed to respond in time. The report also highlights a growing mix of motivations behind DDoS attacks—including competitors, insiders, and state-backed actors.
Key Details
- Germany was the most targeted country, followed by Turkey and China.
- Most attacks were under 10 minutes long and smaller than 1 Gbps—but still effective when defenses weren’t always-on.
- Cloudflare blocked over 700 hyper-volumetric attacks in Q1 alone, including one peaking at 4.8 Bpps.
- Attacker motivations varied: 39% cited competitive disruption, with additional threats from insiders and nation-state actors.
Next Steps
- Prioritize automated DDoS mitigation: Brief, high-speed attacks can succeed if defenses aren’t always on.
Read more on HackRead
2. Breach of Government-Modified Signal App Exposes Risks of Archiving Compliance Tools
Summary A hacker breached TM SGNL, a compliance-focused, modified version of Signal used by U.S. government officials and built by Israeli-American firm TeleMessage. The attacker accessed archived plaintext messages, admin credentials, and contact data—exposing the risks of modifying end-to-end encrypted apps to meet government retention requirements. The app’s design decrypted and stored messages on cloud infrastructure, bypassing Signal’s security guarantees. The breach raises broader concerns about how government agencies adapt consumer secure apps for official use.
Key Details
- The hacker claimed to access TeleMessage’s backend in under 20 minutes and leaked messages, credentials, and screenshots.
- Exposed data included contact information tied to CBP, Coinbase, and U.S. financial institutions—but not Trump cabinet officials themselves.
- Security flaws included hardcoded credentials and the storage of decrypted messages on an AWS server.
- TM SGNL was removed from TeleMessage’s website, and the service has been suspended following the breach.
Read more on HackRead and 404 Media
3. ClickFix Malware Uses Fake Prompts and CAPTCHAs to Trick Users Into Running Payloads
Summary ClickFix is a growing malware technique that disguises itself behind everyday interface elements like CAPTCHA forms, login prompts, or fake software activations. It waits for users to perform what seems like a routine action—then quietly executes a PowerShell script or drops a payload. The approach is highly evasive because the malware activates only after real human interaction, making it difficult for traditional automated scanners to detect.
Key Details
- ClickFix typically hides behind pop-ups, fake account verifications, or browser security warnings, waiting for the user to click or paste a command.
- ANY.RUN sandbox testing showed how clicking a fake CAPTCHA led to execution of a malicious PowerShell script via Windows Run.
- The malware delays action until interaction occurs, avoiding detection by static or passive scanning tools.
- Popular lures include “verify your account,” “fix your system,” or “activate your trial,” all guiding the user to manually trigger the infection.
Read more on HackRead
4. OttoKit WordPress Plugin Exploited to Gain Admin Access
Update – July 14, 2025:
OttoKit has clarified that there is no evidence of real-world exploitation related to CVE-2025-27007 or CVE-2025-3102. The issue was responsibly reported, patched within hours, and users were force-updated to version 1.0.83. You can read the full official statement here.
Summary Two critical vulnerabilities in OttoKit (formerly SureTriggers)—a WordPress automation plugin with over 100,000 installs—have come under active exploitation. Attackers are using a logic flaw in the plugin’s authentication process to create unauthorized admin accounts. One of the bugs allows unauthenticated users to forge a connection with the site, then elevate privileges through the API. These exploits highlight how plugin misconfigurations can silently undermine WordPress site security at scale.
Key Details
- CVE-2025-27007 (CVSS 9.8): Lets attackers forge application connections without proper auth checks, leading to privilege escalation.
- CVE-2025-3102 (CVSS 8.1): Another API-related flaw that attackers are chaining with CVE-27007 to take control of admin functions.
- Attacks were observed just 91 minutes after public disclosure, suggesting bots are scanning for targets en masse.
- Wordfence and Patchstack confirmed active exploitation and recommend immediate patching to version 1.0.83 or later.
Next Steps
- Update OttoKit immediately: All sites running versions ≤ 1.0.82 are at risk of full compromise.
- Audit admin accounts: Check for suspicious users created recently via automation or unknown IPs.
Read more on The Hacker News
5. Trump Picks Private Sector Cybersecurity Veteran for Pentagon CIO Role
Summary President Trump has nominated Kirsten Davies—a cybersecurity executive with experience at Unilever, Estée Lauder, Barclays Africa, HP, and Siemens—to serve as the Department of Defense’s next Chief Information Officer. If confirmed, she would bring deep private-sector expertise to a role that has been vacant since June 2024, during a time when the Pentagon is pushing to modernize and accelerate software acquisition.
Key Details
- The Pentagon CIO role was reinstated as a Senate-confirmable position in 2019 but has seen gaps in permanent leadership.
- The nomination comes as the Pentagon rolls out its “SWIFT” program to overhaul software procurement frameworks.
- Defense Secretary Pete Hegseth has pushed for faster, tech-forward modernization across the DoD.
Read more on The Record
6. Scam Campaign Abuses X/Twitter Ad Loophole to Impersonate CNN and Promote Fake Apple Crypto
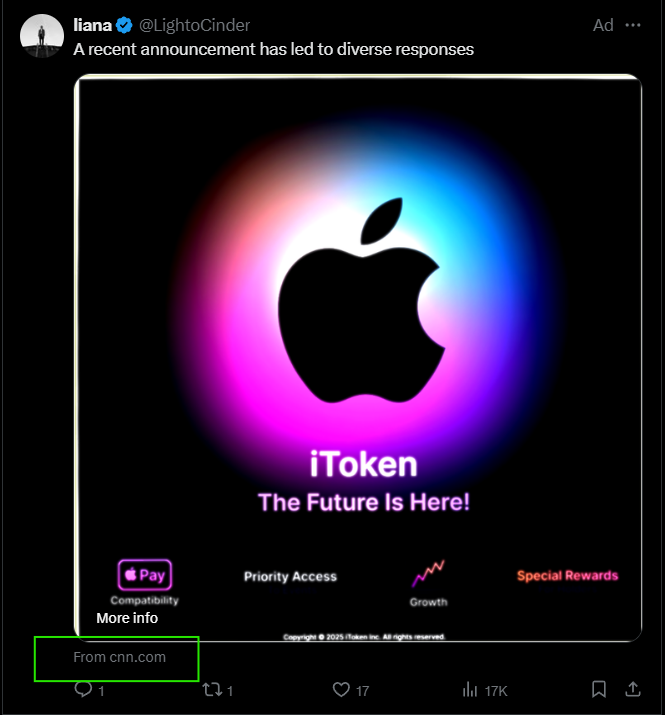
Summary Threat actors exploited a loophole in X/Twitter’s ad system to display “From CNN.com” on scam ads promoting a fake Apple “iToken” cryptocurrency. By manipulating how Twitter’s bot processes redirect metadata, the attackers made scam ads appear legitimate while sending users to phishing sites designed to steal crypto funds. Silent Push analysts found the campaign is part of a broader infrastructure involving at least 90 spoofed domains and reused design elements—suggesting it’s a scalable, ongoing operation likely to reappear under different names.
Key Details
- Attackers used Twitter’s preview system and URL shorteners (e.g., Bitly) to make ads appear as if they linked to CNN.com, while secretly redirecting to domains like ipresale[.]world and itokensale[.]live.
- The scam pages used Apple branding, fake quotes from Tim Cook, and a dashboard prompting users to register and buy “iTokens.”
- Silent Push identified over 90 related domains using shared CSS, favicons, and redirect paths, many hosted via Hetzner and Cloudflare.
- Wallet addresses were set up to accept dozens of cryptocurrencies, including Bitcoin, ETH, XRP, USDT, and others—none of which are recoverable if funds are sent.
- The campaign reused infrastructure across multiple waves, showing signs of rapid redeployment under new domain names.
Next Steps
- Warn users not to trust “From” labels in social media ads: These can be spoofed using preview metadata tricks.
Read more on Silent Push and CyberSecurity News
7. Ransomware Attacks on Food and Agriculture Sector Double in 2025
Summary Ransomware attacks on the food and agriculture industry more than doubled in Q1 2025, with 84 incidents reported versus just 39 in the same period last year. Experts attribute the surge to opportunistic targeting by groups like Clop, Akira, and RansomHub, and warn that the real number is likely higher due to underreporting. The sector’s widespread legacy systems, lack of visibility, and tight supply chains make it an appealing target for both criminal and state-aligned threat actors.
Key Details
- The group Clop was responsible for a large share of Q1 attacks, but other groups continued targeting the sector even after Clop’s activity slowed.
- High-profile incidents include attacks on a South African poultry producer (costing $1 million) and Siberia’s largest dairy plant.
- Food and Ag-ISAC’s Braley said ransomware now accounts for 53% of all attacks on the sector, but many incidents remain unreported.
Read more on The Record
8. “Bring Your Own Installer” Exploit Bypasses SentinelOne EDR via Upgrade Interruption
Summary Researchers at Aon’s Stroz Friedberg uncovered a technique that allows attackers to bypass SentinelOne’s EDR by exploiting its local upgrade process. By carefully timing the interruption of the upgrade—after old protection is stopped but before the new version starts—attackers can leave a system temporarily unprotected. This window allows malware like ransomware to be deployed undetected. SentinelOne has since released updated guidance and mitigation steps to prevent the attack, but the flaw highlights how endpoint tools can be vulnerable to logic abuse even without traditional exploits.
Key Details
- The attack relies on running a different SentinelOne installer version locally, then killing the installer process during the 50–60 second “no protection” window between uninstall and reinstall.
- This technique does not require exploiting the anti-tamper code; it only needs local admin access and a misconfigured policy.
- Stroz Friedberg used the technique in lab conditions to deploy a Babuk ransomware variant during the exposed window.
- SentinelOne has introduced a “Local Upgrade Authorization” toggle to block such behavior and has enabled it by default for new customers.
Next Steps
- Enable the Local Upgrade Authorization setting in SentinelOne to prevent local upgrade/downgrade attempts.
- Audit endpoint policies for misconfigurations that allow local agent changes without central approval.
- Review detection strategies for agent downtime periods—even temporary gaps can be exploited.
Read more on Aon and Dark Reading
9. Email-Based Attacks Dominate Cyber Insurance Claims as Ransomware Stabilizes
Summary According to Coalition’s 2025 Cyber Claims Report, 60% of all claims in 2024 were caused by business email compromise (BEC) and funds transfer fraud (FTF)—far surpassing ransomware in volume. While ransomware remains the most costly attack type, its frequency and severity slightly declined. Meanwhile, BEC losses increased 23%, driven by rising legal and response costs. The report underscores the growing financial toll of email-based social engineering, even as ransomware continues to evolve in sophistication.
Key Details
- Average BEC loss: $35,000; average FTF loss: $185,000; average ransomware loss: $292,000.
- 29% of BEC incidents also resulted in FTF attacks, often involving spoofed emails from vendors or executives.
- Ransomware claims dropped 3% in frequency and 7% in severity; Akira was the most common variant, while Black Basta had the highest average demand ($4M).
Next Steps
- Prioritize protection against BEC and FTF attacks: Invest in email security, MFA, and employee awareness to mitigate socially engineered fraud.
Read more on Dark Reading and Coalition
10. Trump Administration Proposes $491M Cut to CISA Budget
Summary The Trump administration has proposed slashing nearly half a billion dollars from the Cybersecurity and Infrastructure Security Agency (CISA) budget, a 17% reduction aimed at “refocusing” the agency on its core mission of cyber defense. The proposed cuts would eliminate programs tied to misinformation, international engagement, and public outreach — which the administration claims are “wasteful” or politically biased. Critics warn that dismantling these functions could severely undermine national cybersecurity, especially during an election year and amid rising global threats.
Read more on SecurityWeek, National CIO Review, and SiliconANGLE
11. California Fines Retailer for Blocking Opt-Outs Under Privacy Law
Summary The California Privacy Protection Agency (CPPA) has fined menswear retailer Todd Snyder Inc. $345,000 for violating state privacy law by blocking consumer opt-out requests and demanding excessive personal information. The agency said the company’s flawed privacy portal and misconfigured backend prevented users from exercising their right to stop the sale or sharing of personal data—highlighting how poor technical implementation can turn into legal liability under the CCPA and CPRA.
Key Details
- The company was found to require more personal data than necessary to process opt-out requests, a direct violation of California privacy rules.
Next Steps
- Audit your privacy request flow: Ensure consumers can exercise opt-out rights without unnecessary friction or data demands.
- Align technical infrastructure with legal intent: A misconfigured form or backend can lead to enforcement action.
Read more on The Record
12. Fake Resumés Target HR Teams With Updated More_eggs Malware
Summary A new spear phishing campaign is targeting HR staff with fake job applications that deliver an upgraded version of the More_eggs backdoor. Sent via job platforms or messaging services, the campaign tricks recruiters into downloading malicious ZIP files disguised as resumés. These files exploit a temporary lapse in vigilance to install polymorphic malware that evades sandboxing, then launches a stealthy backdoor for credential theft and further compromise.
Key Details
- The attack uses a .LNK file disguised in a ZIP, along with a decoy image, and relies on user interaction (e.g. clicking a CAPTCHA).
- Server-side polymorphism ensures each download is unique, helping evade static detection.
- The malicious code uses legitimate Windows tools like
ie4uinit.exefor execution, distracting the user with WordPad while launching the backdoor.
Next Steps
- Train HR staff to be cautious with resumés, especially ZIPs, .LNK, VBS, or ISO file types—even if they include a password.
Read more on CSO Online
13. M&S, Co-op, and Harrods All Hit by Cyber Incidents
Summary Three of the UK’s best-known retailers—Marks & Spencer, the Co-op, and Harrods—have suffered cyber incidents within the same two-week period, causing payment issues, online order disruptions, and internal system lockdowns. While the incidents haven’t been officially linked, analysts suggest possible shared supplier compromise or increased sector-wide threat activity. M&S’s incident alone may cost the company £30M in profit, highlighting just how quickly operational disruptions can turn into major financial losses in retail.
Key Details
- M&S was hit around April 22, leading to contactless payment issues, paused Click & Collect, and halted web/app orders. Empty shelves and system outages followed.
- Analysts suggest Scattered Spider may be behind the M&S breach, which impacted store operations and remote work access.
- Co-op confirmed a cyberattack on April 30, shutting down parts of its IT systems. Staff were told to remain on camera and avoid posting sensitive info in Teams.
- Harrods reported an attempted breach on May 1 and restricted internet access across its sites as a precaution. Stores remained open.
Read more on Cyber Magazine
14. The Most Interesting Cybersecurity Product Launches from RSA 2025
Summary AI dominated RSA 2025, where nearly every major cybersecurity vendor showcased how artificial intelligence is reshaping threat detection, response, and automation. From LLM firewalls to autonomous SOC agents and smarter identity protection, vendors are embedding AI deeper into their platforms—not just for alerts, but for action. Here are the standout launches security leaders should know about.
Key Product Announcements
- Palo Alto Networks – Prisma AIRS: Enhanced by the acquisition of Protect AI, this platform adds AI-powered detection and response to protect AI infrastructure itself. Also announced Cortex XSIAM 3.0 for next-gen SOC automation.
- Cisco – Foundation AI Security Model: An open-source initiative to standardize safe AI deployment practices. Also added agentic AI and automated attack verification to Splunk and XDR products.
- ServiceNow – AI Security Operations: Real-time, AI-powered incident response tools integrated with Cisco infrastructure. Aimed at speeding up resolution through collaborative AI agents.
- CrowdStrike – Falcon Privileged Access: Identity-focused access protection module built into the Falcon suite, plus automation upgrades to Falcon SIEM and Charlotte AI for faster identity threat detection.
- Check Point + Illumio – Smart Cyber Defense Platform: Combines threat prevention with Illumio’s microsegmentation to boost Zero Trust and contain breaches before they spread.
- Armis – Centrix Platform + Vulnerability Intelligence DB: Delivers unified attack surface visibility and real-time risk insights, plus a new database to help prioritize vulnerability remediation.
- SentinelOne – Purple AI Athena: An autonomous SOC agent that mimics analyst reasoning to investigate and remediate threats in real time.
- Darktrace – Cyber AI Analyst Upgrades: Introduced new LLM-trained AI models to enhance investigation accuracy and reduce SOC workload. Claims 90M automated investigations in 2024.
- Huntress – ITDR & SIEM Expansion: New features for detecting credential abuse (e.g. malicious OAuth apps and inbox rules) and a fully managed SIEM with 20+ integrations.
- Abnormal AI – AI Phishing Coach & Data Analyst: AI agents for personalized phishing awareness training and transforming raw security data into actionable insights.
- Fortinet – Enhanced FortiAI: FortiAI’s updated version integrates AI across the Fortinet Security Fabric to stop advanced threats and support secure AI adoption.
- Akamai – Firewall for AI: A new firewall designed specifically for LLMs and AI apps, blocking prompt injection, data leaks, and malicious outputs in hybrid environments.
Read more on CSO Online
15. Why CISOs Need Wartime Contingency Planning on the 2025 Agenda
Summary Amid escalating global tensions—from Ukraine to South Asia—CISOs and C-suite leaders are being urged to treat war planning as an operational necessity, not just a government concern. In the UK, Prime Minister Keir Starmer ordered a review of national contingency plans to prepare for the possibility of “full-out war,” signaling that wartime disruption is now a leadership-level consideration. Organizations are being advised to assess exposure to geopolitical hotspots, refresh crisis playbooks, and prepare for infrastructure disruption and workforce loss in regions that support global operations.
Key Details
- RSA speakers Tom Cross and Greg Conti urged tech companies to create formal “war plans,” as a great power conflict is no longer an abstract threat.
- The India-Pakistan escalation and Starmer’s call to update UK contingency plans prompted renewed attention to outdated corporate playbooks.
- Conflict zones like India and Pakistan house critical IT services, and population displacement could trigger infrastructure breakdowns and workforce disruption.
- NATO’s Admiral Rob Bauer warned business decisions now carry strategic consequences and advised building secure, redundant infrastructure with wartime resilience in mind.
Next Steps
- Review and modernize your contingency plans: Emergency response procedures should be updated at least annually—not every decade.
- Assess geopolitical exposure across third-party ecosystems: This includes outsourced operations, cloud regions, and at-risk vendor geographies.
Read more on CSO Online
16. NATO’s Locked Shields 2025 Simulates Massive Infrastructure Attacks
Summary Locked Shields 2025—hosted by NATO’s Cooperative Cyber Defence Centre of Excellence (CCDCOE) in Estonia—brought together 4,000 cybersecurity professionals from 41 countries in the world’s most complex live-fire cyber defense exercise. Teams were tasked with defending 8,000 virtual systems across military, telecom, and critical infrastructure scenarios, while also managing disinformation, legal challenges, and geopolitical pressure. The exercise reflects how blurred the lines have become between cyber war, crisis communications, and infrastructure resilience.
Key Details
- 17 blue teams participated, defending against thousands of coordinated attacks in a simulation environment managed by Estonia’s CR14 Foundation.
- This year’s exercise added scenarios involving quantum computing, AI, and coordinated disinformation campaigns.
- Participants had to navigate legal, operational, and communications challenges—testing full-spectrum cyber readiness.
- CCDCOE Director Mart Noorma called Locked Shields a training ground for defending both national networks and the “essential services societies depend on.”
Read more on SecurityWeek
17. AI-Generated Victim Avatar Used in Road Rage Sentencing Raises Ethical Questions
Summary In a first-of-its-kind moment, an Arizona judge accepted a victim impact statement delivered by an AI-generated avatar of a man killed in a 2021 road rage shooting. Created by the victim’s sister, the avatar of Christopher Pelkey was trained to look and sound like him and spoke words scripted by his family, including a direct message of forgiveness to the shooter. The judge was visibly moved and imposed the maximum sentence. The case highlights the emotional and ethical complexity of using AI in courtroom proceedings—especially when speaking on behalf of the dead.
Key Details
- The avatar was created using Stable Diffusion (with LoRA tuning) and voice cloning tools, and was clearly labeled as AI-generated.
- Its use was permitted under Arizona’s victim rights laws, which let families choose the format of impact statements.
- The video combined real clips of Pelkey with the AI-generated likeness delivering a scripted message to the court and to the shooter, Gabriel Horcasitas.
- While the judge praised the emotional impact of the message, some experts and observers raised concerns about whether it was appropriate to “put words in a dead man’s mouth.”
Read more on 404 Media
18. JPMorgan’s Open Letter to SaaS Providers: Security Must Come Before Features
Summary In a rare public letter, JPMorgan Chase CISO Patrick Opet called on SaaS and software vendors to radically rethink their security priorities. The letter warns that modern SaaS delivery models have created dangerous concentration risk and eroded traditional security boundaries—leaving global infrastructure exposed to systemic failures. JPMorgan urges suppliers to stop prioritizing speed and features over built-in security, calling today’s third-party integration models a “single-factor explicit trust” architecture that attackers are actively exploiting.
Key Details
- Modern SaaS integrations often blur internal/external boundaries and rely on oversimplified OAuth-based trust, increasing risk of abuse.
- The firm warns that compromised tools with “read-only” API access can escalate into full internal compromise due to flawed architectural assumptions.
- Fourth-party dependencies and AI-powered integrations are amplifying this risk across sectors faster than security controls are evolving.
- Suggested mitigations include confidential computing, customer self-hosting, and “bring your own cloud” deployments for greater isolation.
Next Steps
- Push vendors for secure-by-default controls and transparency: Demand evidence of controls that go beyond annual compliance reports.
- Start rejecting high-risk integration patterns unless stronger, verifiable alternatives (like policy isolation or confidential computing) are in place.
Read the full open letter on JPMorgan
