How to implement the Estonian Information Standard (E-ITS) with Kordon?
E-ITS Implementation Process with Kordon
Kordon GRC platform is as easy to use as a spreadsheet but built for implementing frameworks like the Estonian Information Security Standard (E-ITS).
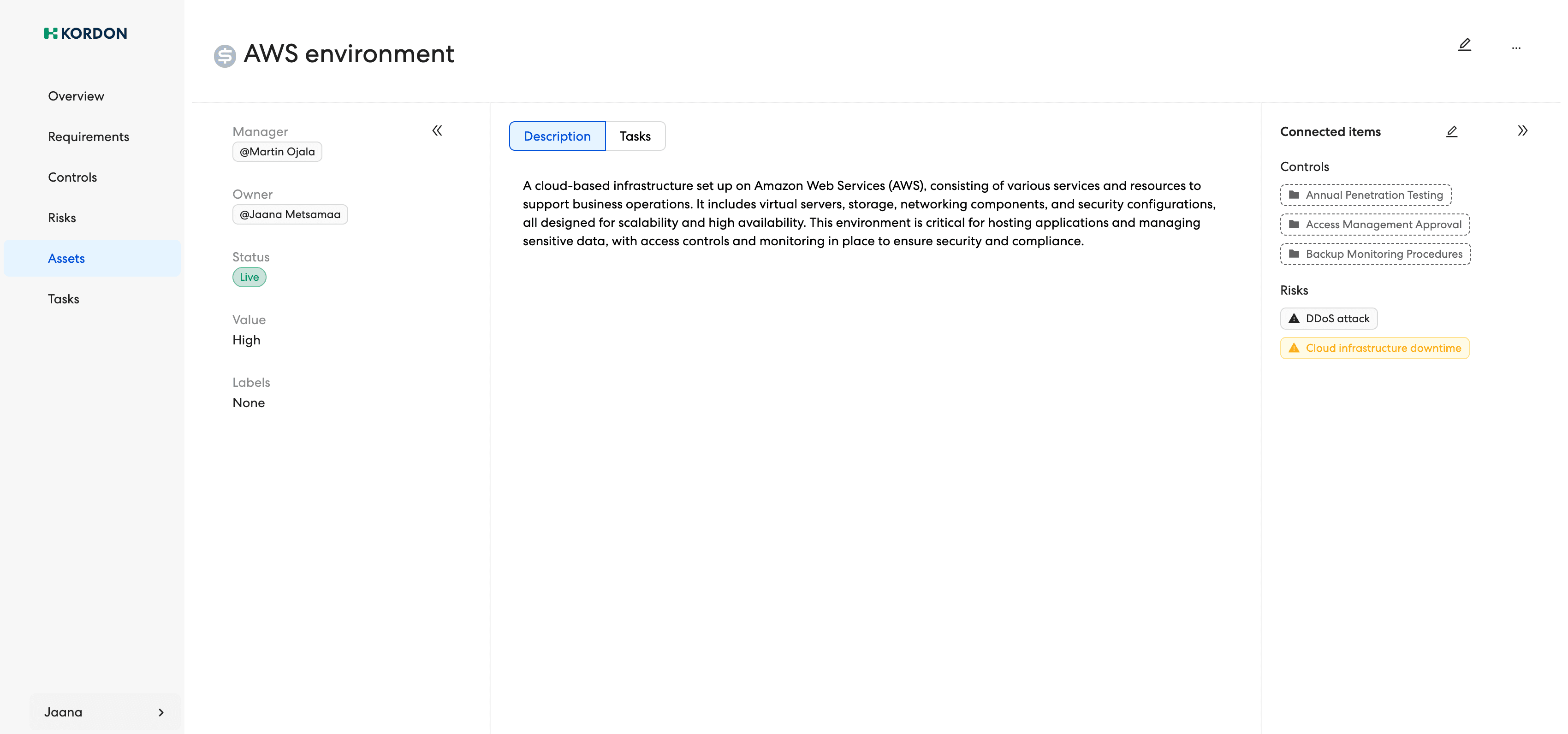
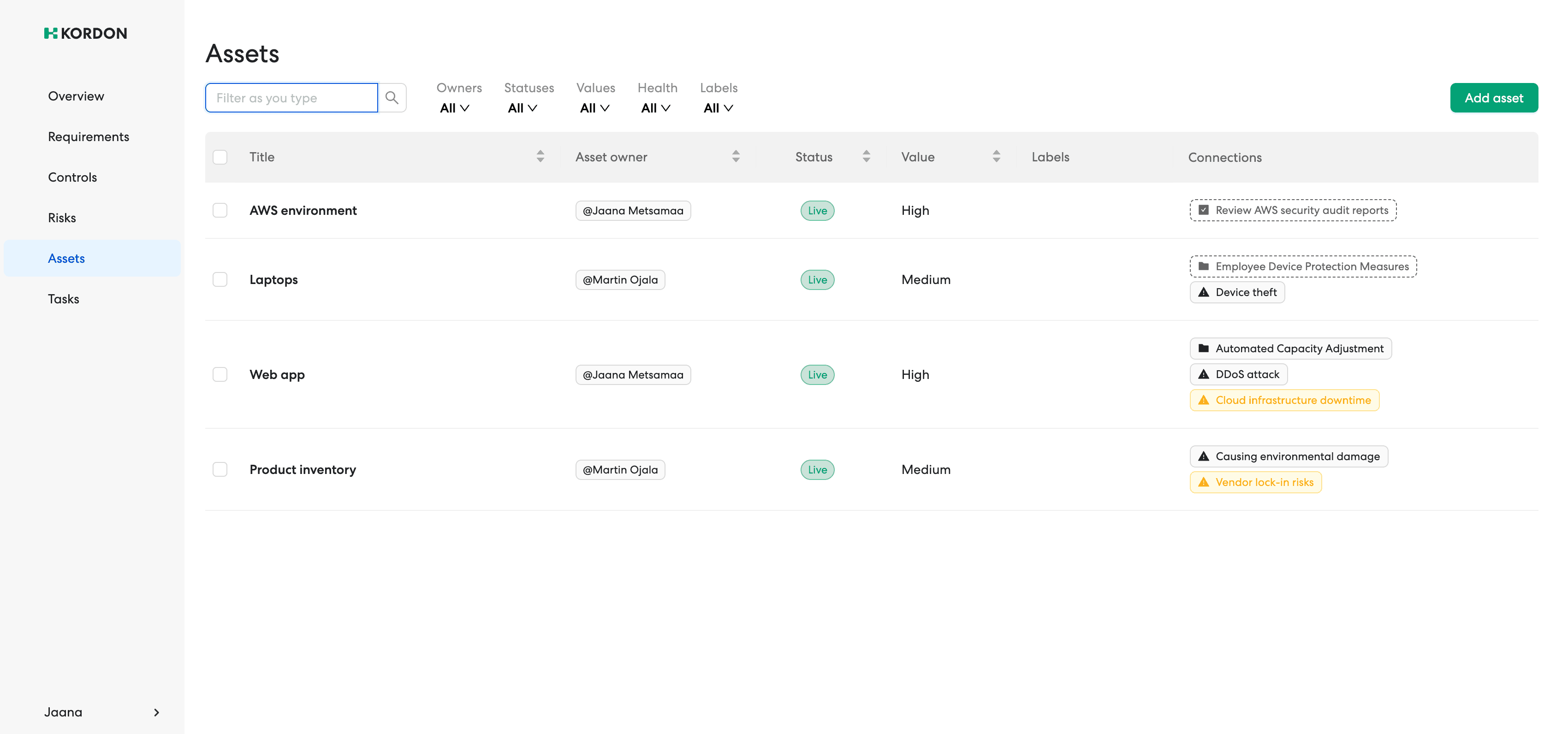
Documenting assets and their risks
E-ITS implementation starts with the documentation of the organisations assests, assessing their protection requierment, and the associated risks.
Choosing applicable standard measures
Not all E-ITS standard measures need to be implemented by everybody. Based on the assets protection requierments and risk, the next step is to choose which E-ITS measures are applicable.
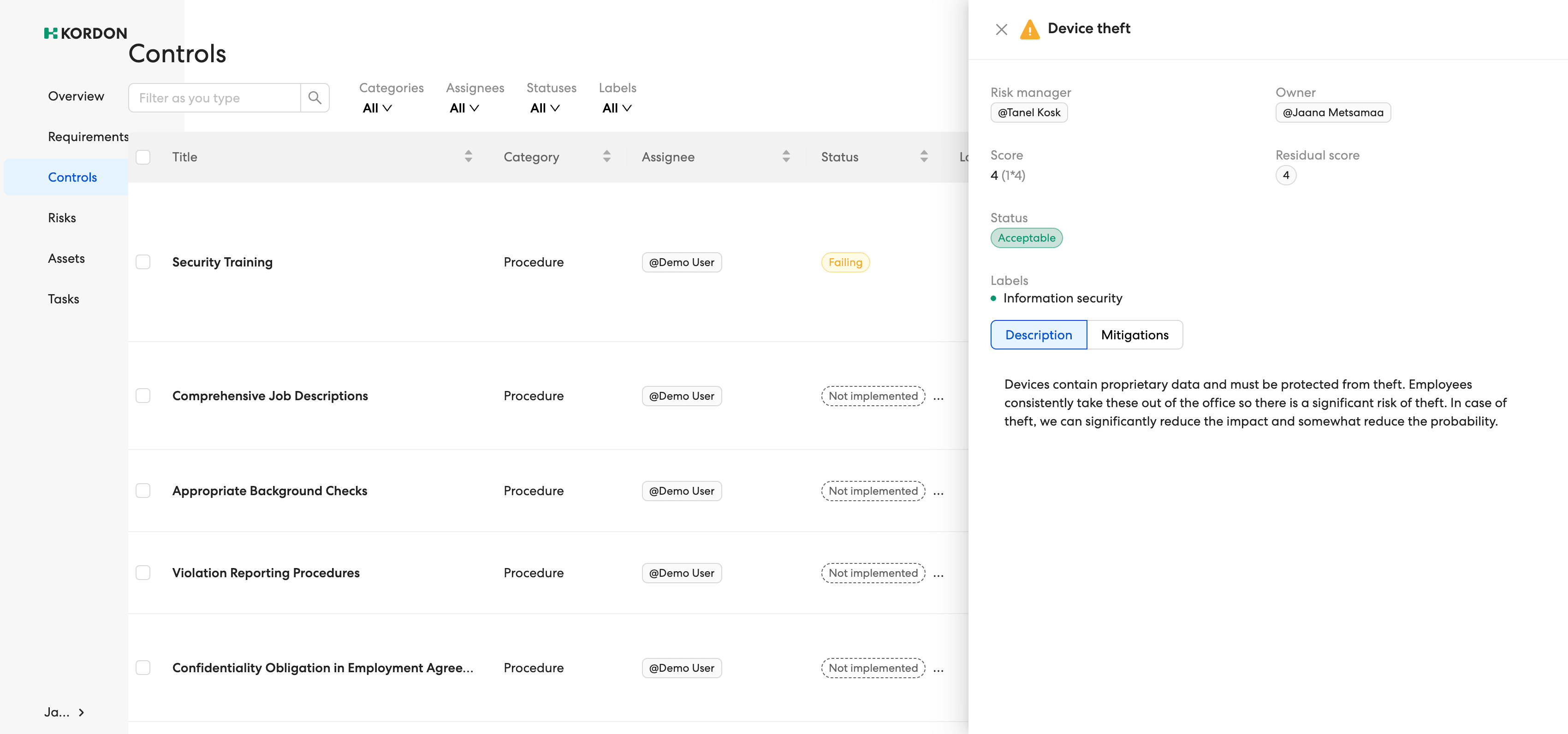
Implementing internal security controls
Based on the applicable standard measures, and the risk registry, the security policies and controls are designed.
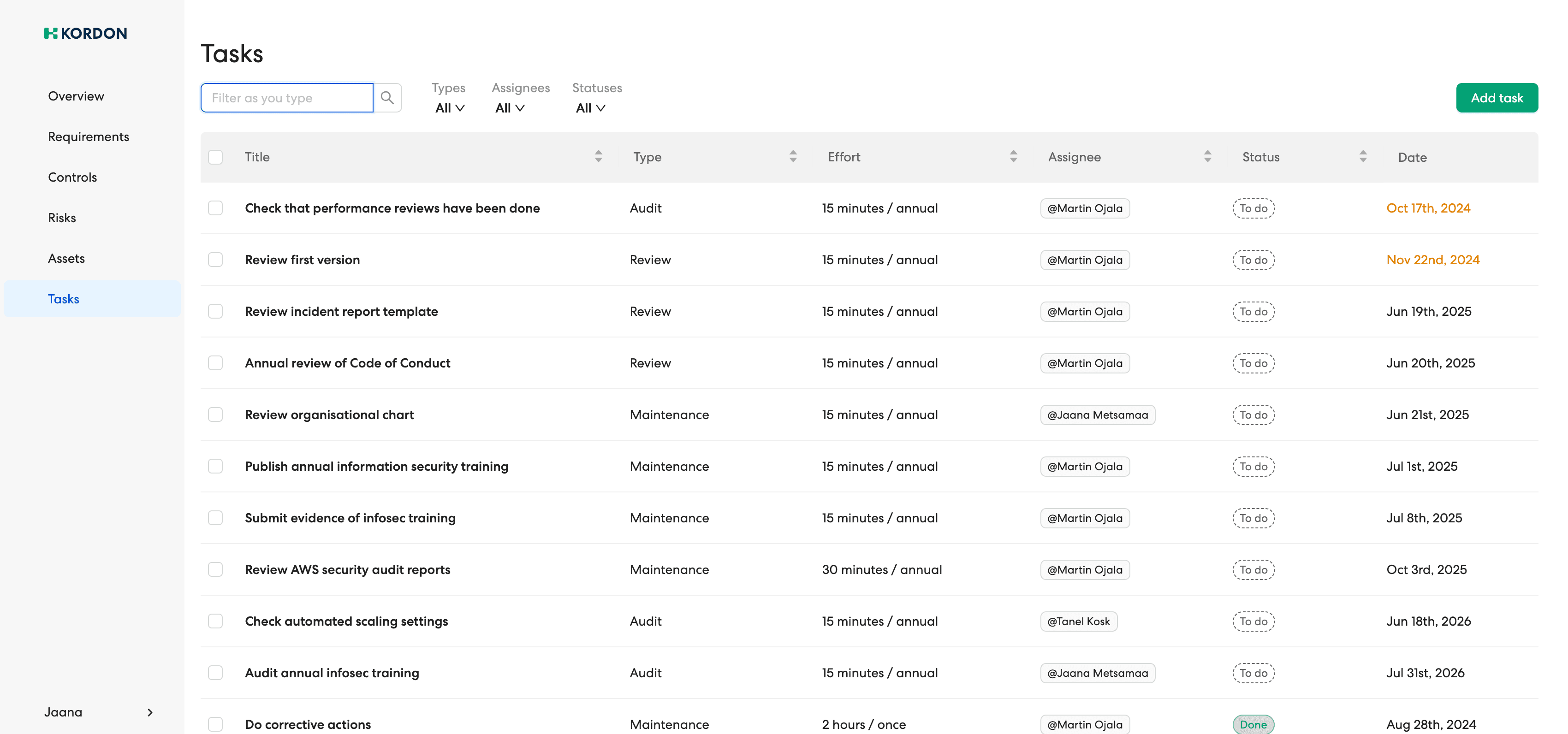
Continuous management
The regular completion of activities set out in the policies and controls for the information security program to function per its design.
Regular audits and continuous improvements
Regular internal and external audits to discover caps and opportunities for improvements.
Frequently Asked Questions
How is Kordon different from other tools in implementing the Estonian Information Security Standard (E-ITS)?
Kordon is uniquely designed to handle the cyclic and iterative processes of information security, unlike other tools which may only mark measures as implemented. It integrates asset management and risk management modules to ensure real-time protection and compliance, simplifying audits and ensuring continuous operation.See more on the Kordon vs Cybsis for E-ITS comparison page.
What value does Kordon bring during E-ITS audits?
Kordon simplifies the audit process by allowing all security activities and evidence to be managed and documented within the platform. Auditors can be added as read-only users, significantly reducing the audit burden on organizations by providing direct access to necessary documents and compliance reports
How does Kordon integrate with other IT systems for a seamless E-ITS implementation?
Kordon can integrate effortlessly with existing IT systems through its REST API and native integration with automation platforms like Zapier. This integration capability ensures that data flows seamlessly between Kordon and other platforms, maintaining up-to-date and accurate information across systems.
Can Kordon support both cloud and on-premise solutions for E-ITS implementation?
Yes, Kordon offers both on-premise and cloud solutions, making it suitable for organizations of different sizes and IT capabilities. This flexibility helps organizations maintain their information security with whatever infrastructure they have in place.
Which phases of E-ITS compliance does Kordon support?
Kordon supports the entire lifecycle of E-ITS implementation from asset mapping, risk assessment, and control measure implementation to regular compliance checks and audit readiness. It also allows the integration of other frameworks like ISO 27001, enabling efficient management without duplication of efforts.
Experience the Kordon GRC platform Advantage
With Kordon, you're not just ticking boxes—you're building a robust security program with daily visibility into where your company stands.
Goodbye Excel chaos
Centralise your entire security program in one intuitive platform, eliminating the need for scattered spreadsheets and last-minute scramble.
Big picture
Get real-time insight into how your security program covers framework requirements and discover the next most impactful action to strengthen your security posture.
Focus on actual security, not busywork
Free up your team's time to concentrate on strategic improvements rather than administrative tasks.
Time-saving automation
Reduce compliance workload by up to 80% through evidence collection and task automation.
Faster audits
As read only users, auditors can get everything they need from the app. No more sending documents back and forth.
Proactive compliance
Shift from reactive audit preparation to continuous compliance, with automated collection of evidence.
Packed with features
Control Management
Work with the controls you already have in place or use Kordon's templates as starting point. Connect controls with requiermens from one or multiple frameworks and reduce duplication of effort.
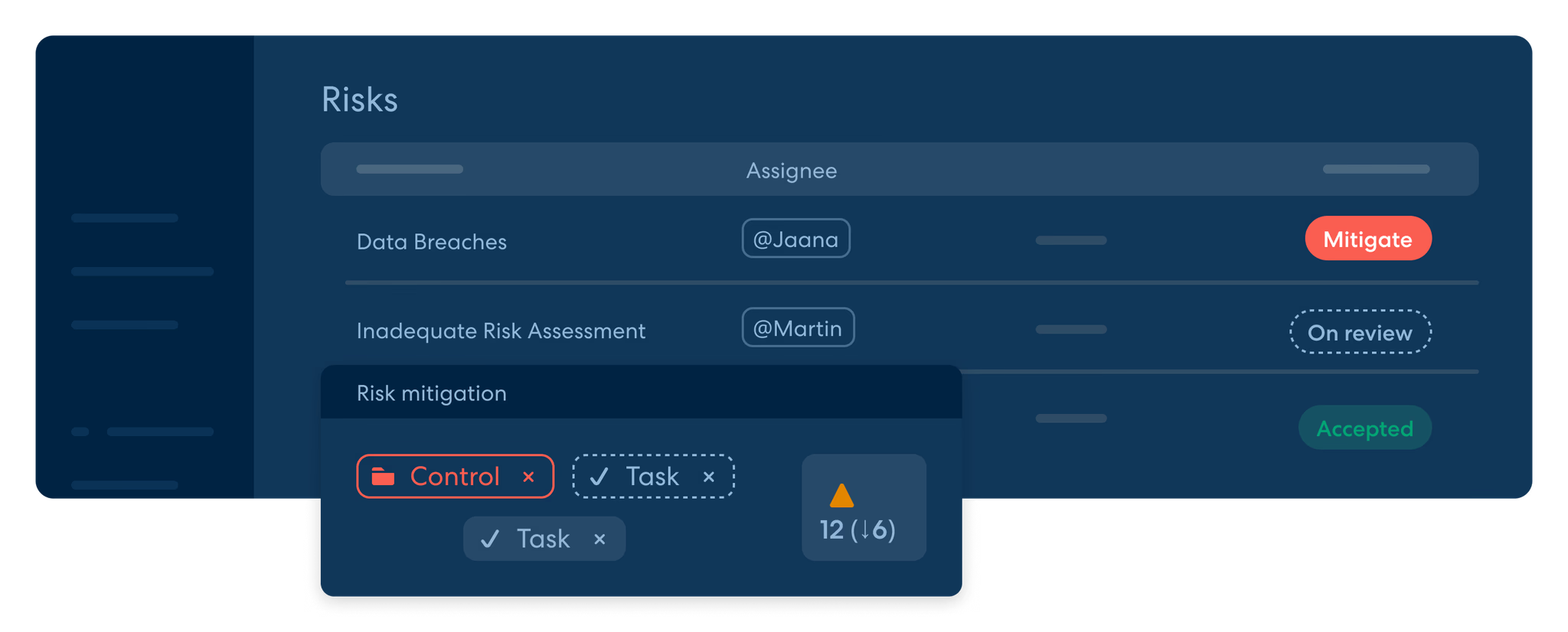
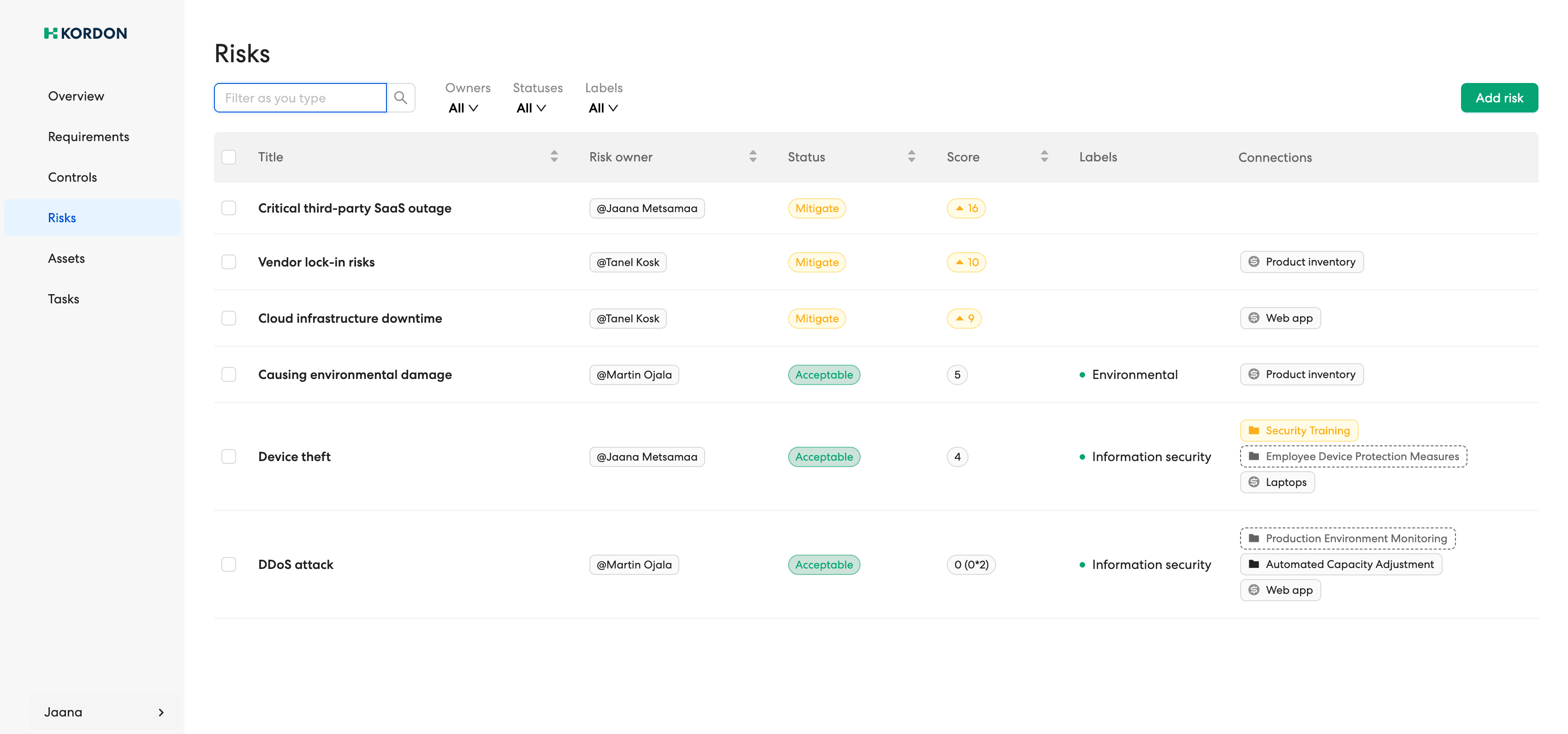
Risk Management
Go beyond just documenting risks and gain live insight into how well your risk management and controls are working. Risk management in Kordon links risks to dynamic controls to effectively monitor and reduce threats.
Risk Management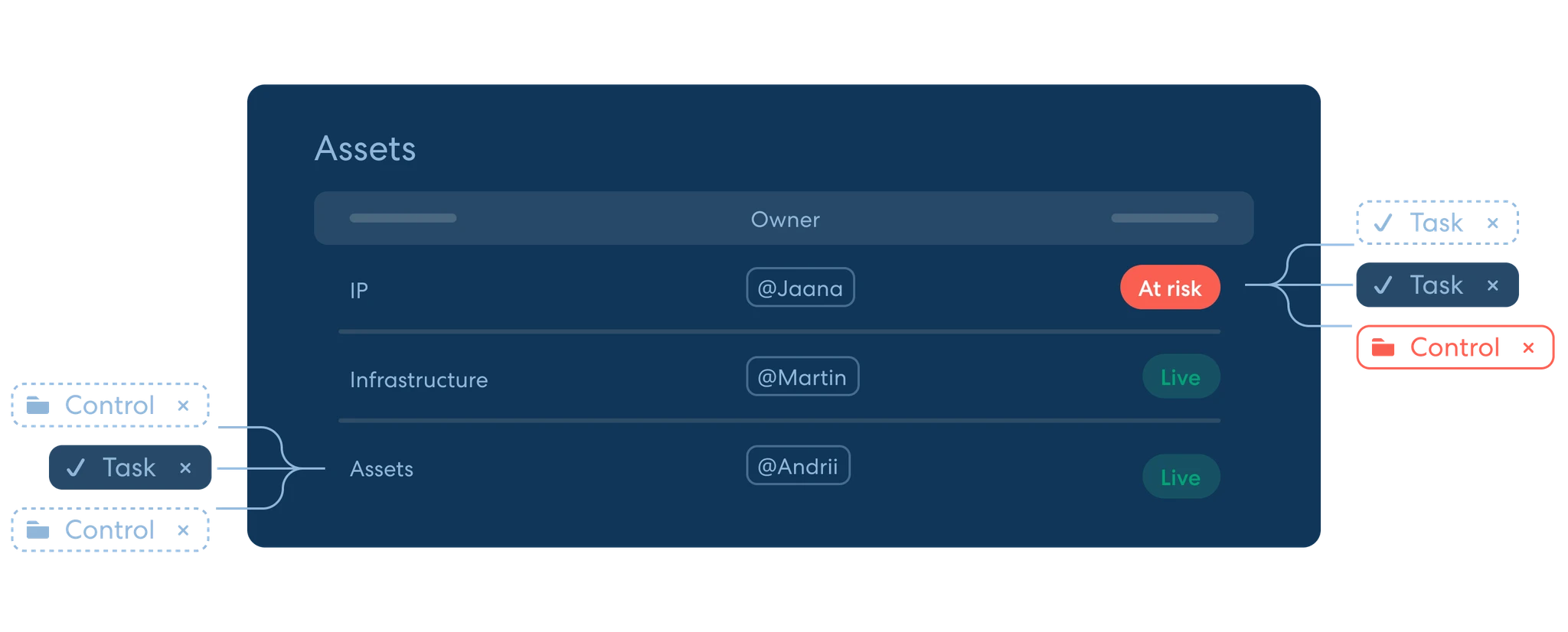
Asset Management
Connect assets to both dynamic controls and associated risks to manage, monitor and protect your assets based on the actual effectiveness of your security measures.
Asset Management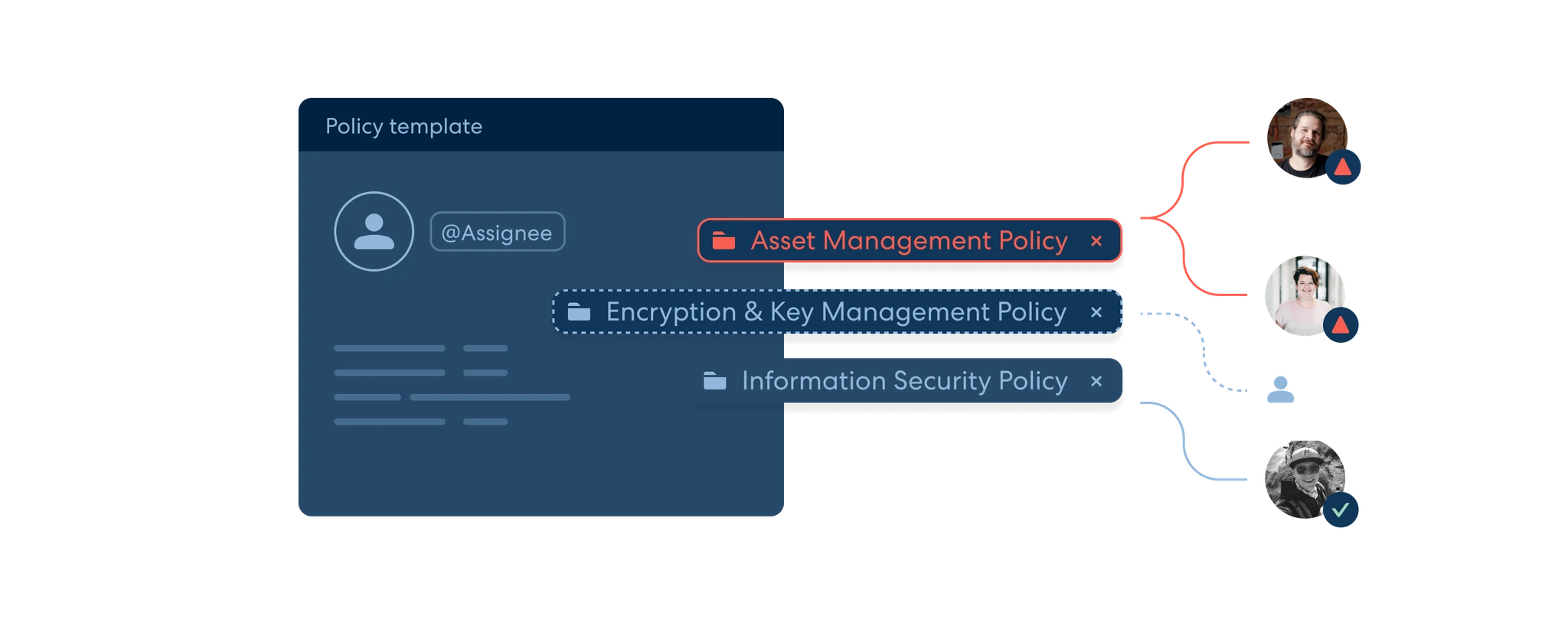
Policy Management
Take control over your policy process from drafting and reviewing to employee acceptance. Start with one of our 20+ policy templates or bring your own.
Policy ManagementAutomated Evidence Collection
Reduce compliance workload by up to 80% through automated task assignments and reminders.
Powerful API
Extend the capabilities of Kordon using the powerful API. Automate workflows further by integrating Kordon with your other systems.
Advanced Permissions
With our flexible visibility and permission system, everyone can see and do exactly what they need, not more, not less.
Kordon GRC platform in action
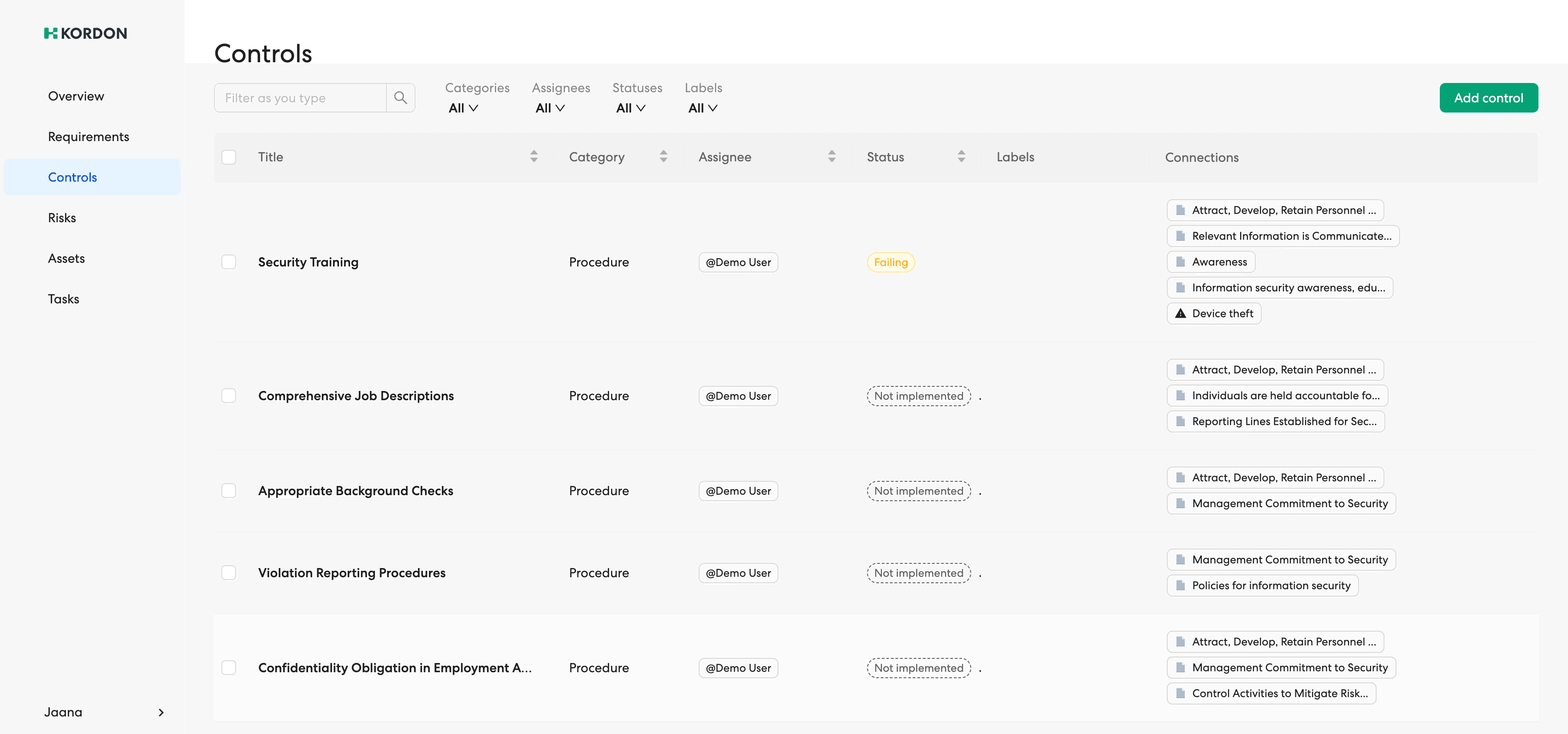
GRC Resources
Learn more about information security management system related topics in compliance with frameworks like ISO 27001, ISO 9001, ISO 42001 , NIS2 and DORA.