07 juuni
A major-number leap for a major-league release
Version 1.8.0 isn’t “just another point update.” It’s a fundamental upgrade for organisations that run their compliance programme on Kordon. Two flagship features Universal Changelog ja Business Process Management arrive alongside a helpful bug-squish, setting the stage for tighter governance, sharper audits, and calmer nights for information security program managers everywhere.
Universal Changelog
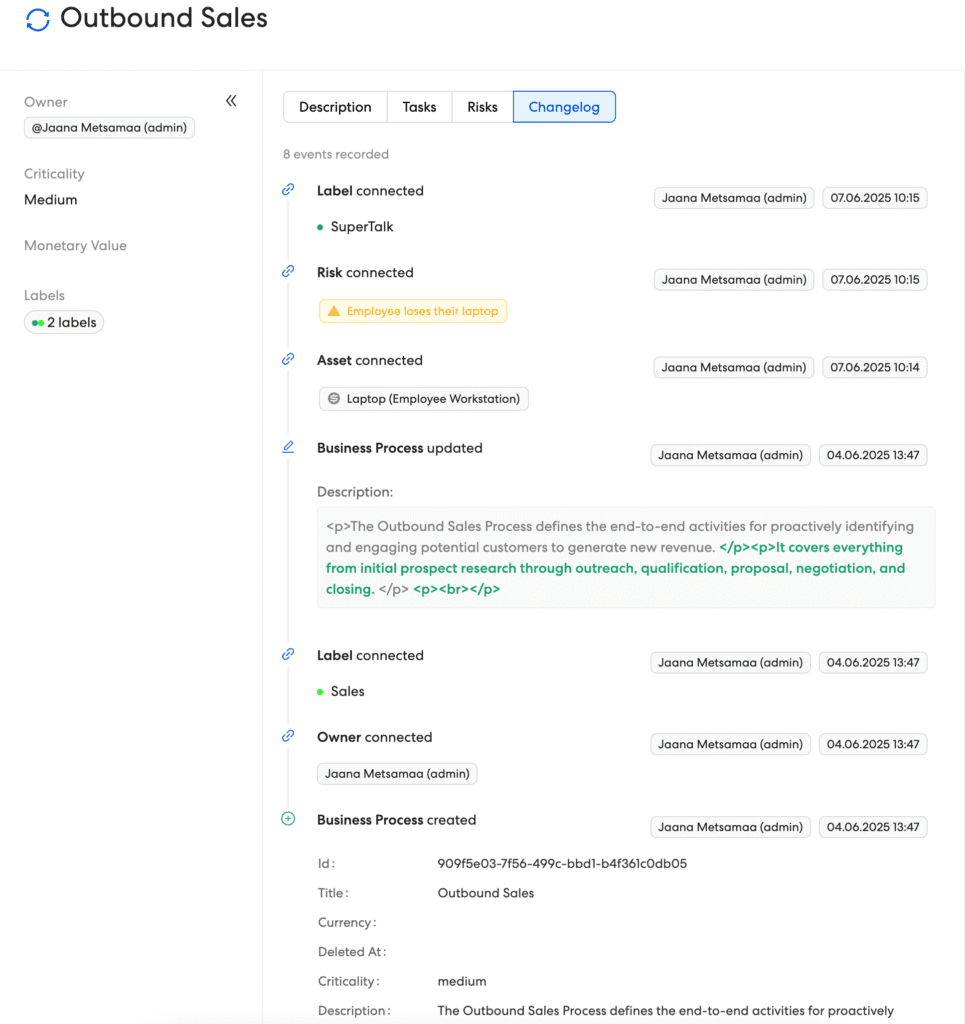
Every asset. Every tweak. Every keystroke—captured.
Remember the auditor’s favourite questions:
- Who changed this policy?
- When did it happen?
- What exactly changed?
Followed by the dreaded, Can you prove it? Kordon’s new Universal Changelog answers all of them, automatically.
| What it captures | Why it matters |
|---|---|
| Who pressed “Save” | Individual accountability and separation of duties |
| When they did it | Precise timeline for audits, incident forensics, and ISO 27001 clause 6.2 evidence |
| What was modified | See exactly what was changed and see the diff view of additions / removals within large texts. |
| Where the change originated | We know the user of course, but also their IP address, closing the loop on insider-risk investigations |
Why granular change logs super-charge your ISMS
- Audit-readiness on autopilot – External assessors can trace every revision without e-mailing your team for screenshots.
- Stronger risk posture – Spot unauthorised or out-of-cadence edits quickly, reducing mean-time-to-detect.
- Regulatory alignment – Frameworks like ISO 27001, SOC 2, and DORA require “documented information” and “change control.” Universal Changelog ticks those boxes natively.
- Institutional memory – People leave; organised information and metadata doesn’t. Kordon keeps the entire ISMS in a single place, the new changelog also can tell the story how the program has evolved over time.
🏢 Business Process Management
Map how your organisation really works—and secure it.
Policies and controls are only effective when they’re grounded in day-to-day operations.
- Document processes end-to-end, from “Customer On-boarding” to “Incident Response.”
- Assign clear owners so responsibility never falls through the cracks.
- Link supporting assets & vendors to each process, revealing hidden dependencies.
- Associate risks You invest risk management effort where it protects business value, not where a checklist told you to.
🐛 Bug Squish (Frameworks Edition)
Frameworks on the Overview page are back in alphabetical order. Again. Sometimes bugs are zombies—this one finally stayed in its grave. 🧟♂️ We hope …
Ready to level-up your ISMS?
If you’re Kordon instance is hosted by us, it’s already up to date and has the latest version.
If you like to run your GRC application on-premises, then you know the drill and you can upgrade yourself as per usual.
