23 veebr.

Latest Interesting Cybersecurity News – 23-02-2026
Latest interesting cybersecurity news from February 2026
16 veebr.

Latest Interesting Cybersecurity News of the Week Summarised – 16-02-2026
Latest interesting cybersecurity news from February 2026
09 veebr.

Latest Interesting Cybersecurity News of the Week Summarised – 09-02-2026
Latest interesting cybersecurity news from February 2026
02 veebr.

Latest Interesting Cybersecurity News of the Week Summarised – 02-02-2026
Most interesting cybersecurity news from last week of January 2026.
26 jaan.

Cybersecurity News Worth Your Attention this Week Summarised – 26-01-2026
Here are the latest cybersecurity stories from January 2026: I go through about 25 cybersecurity news portals and blogs every week and pull out the most interesting stories.
21 jaan.
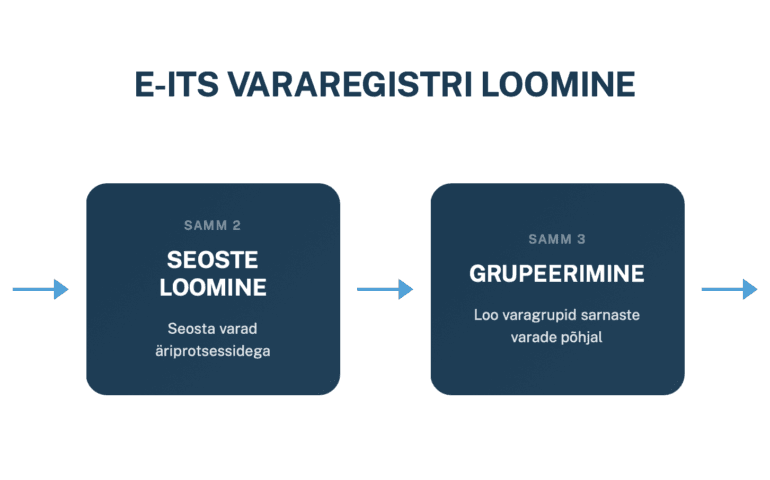
Detailne juhend: Kuidas luua E-ITS varade ja teenusepakkujate register
Eelmises postituses rääkisime sellest, kuidas äriprotsesside kaardistamine aitab aru saada, mida organisatsioon tegelikult teeb. Nüüd, kui me teame mida me teeme, on aeg küsida järgmine kriitiline küsimus: millega me seda teeme? Siin tulevadki mängu vara- ja teenusepakkujate registrid. Sa ei
