06 okt.
If you’ve ever needed examples of what could happen with cyber attacks in “traditional” non-techy companies, this week has two examples. Actually they are good cautionary tales in any industry.
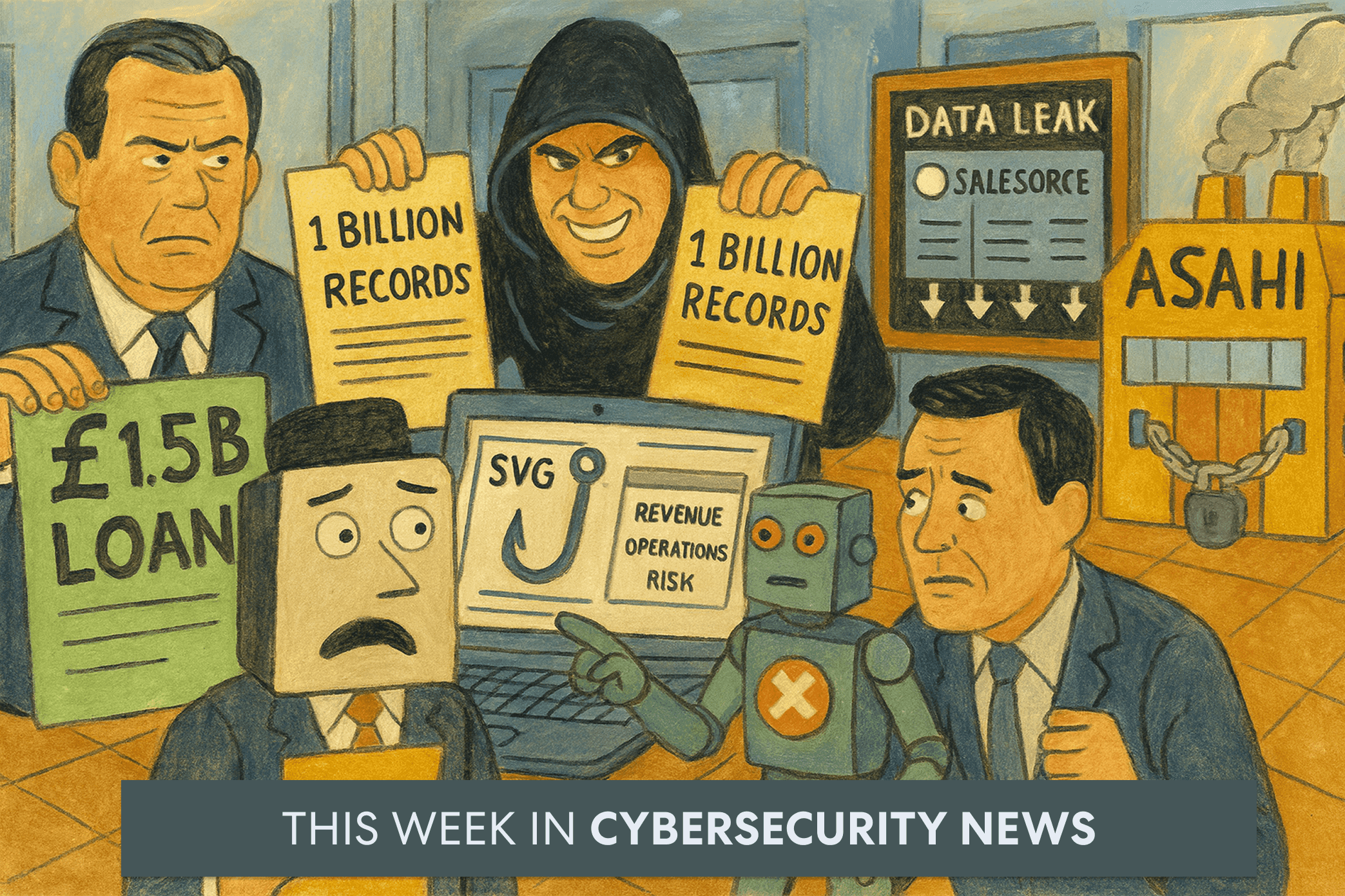
The UK goverment, needed to underwrite a £1.5 B loan to help Jaguar restore it’s supply chain because it was not properly insured against cyber attacks and the japanese beer giant Asahi needed to close down 30 factories and postpone the launch of new products.
1. Salesforce Blackmailed With 1 Billion Customer Records
Scattered Spider launched a dark-web leak site listing dozens of major organizations, including Salesforce itself, claiming to hold over 1 billion stolen records and demanding a ransom by October 10. "At this time, there is no indication that the Salesforce platform has been compromised, nor is this activity related to any known vulnerability in our technology,” the spokesperson said.
Key Details
- Scattered Spider claims to hold >1 billion records and threatens to share data publicly if Salesforce doesn’t pay.
- The leak site lists dozens of firms across airlines, retail, insurance and tech, plus Salesforce.
- Salesforce says no platform vulnerability is implicated and has engaged law enforcement and external experts.
- Google’s threat intelligence group links thefts to voice-phishing (vishing) attacks, not a Salesforce breach.
Read more at The Record
2. Microsoft Flags AI-Generated Phishing Campaign Embedded in SVG Files
Microsoft Threat Intelligence detected and blocked an August 18 credential-phishing campaign that used AI-crafted code hidden inside .svg files disguised as business dashboards to steal log-in credentials. By embedding payloads with common business terms and leveraging Large Language Models for obfuscation, attackers bypassed traditional filters—only to be caught by Defender for Office 365’s AI behavioral analysis.
Key Details
- The .svg attachment appeared to be a 6-page PDF but contained scriptable elements and embedded JavaScript.
- Malicious payload encoded using business terms like “revenue,” “operations,” and “risk” to blend into analytics dashboard structure.
- Attackers used a compromised small-business email account, sending self-addressed messages with real targets BCC’d.
- Microsoft’s Security Copilot flagged the code as AI-generated due to over-engineered structure and verbose naming.
Next Steps
- Block or quarantine incoming .svg attachments by default
- Implement email rules to flag self-addressed messages with hidden BCC recipients
Read more at HackRead.com
3. Microsoft Outlook Blocks Inline SVG Images to Curb Phishing Risk
Starting mid-October 2025, Outlook for Web and the new Outlook for Windows will no longer render inline SVG images, showing blank spaces instead, to mitigate cross-site scripting and phishing attacks that abuse SVG’s scriptable nature. Classic SVG attachments remain viewable, and the change impacts fewer than 0.1% of all images, fitting into Microsoft’s broader effort to tighten attachment security.
Key Details
- Rollout began early September and completes for all customers by mid-October 2025.
- Inline SVGs often used by PhaaS platforms (Tycoon2FA, Mamba2FA, Sneaky2FA) to host phishing forms or malware.
- SVG attachments sent as classic files remain supported and viewable from the attachment well.
Read more at BleepingComputer
4. Third-Party Support Breach Exposes Discord User PII and Photo IDs
A compromised customer-support vendor allowed attackers to steal names, emails, support chats, IP addresses, partial billing details and a small number of scanned government-issued IDs from users who contacted Discord.
Discord’s core systems and full payment data remain secure.
Key Details
- Breach origin: unauthorized access to third-party ticketing system (reported via Zendesk).
- Data accessed: full names, usernames, emails, support messages, IPs, payment type, last four CC digits.
- Sensitive IDs: small subset of driver’s licenses and passports submitted for age verification.
- Unaffected data: full credit card numbers, CCV codes, account passwords, private platform chats.
Next Steps
- Enforce MFA and session timeouts for all third-party integrations.
Read more at Cybersecurity News, BleepingComputer
5. Red Hat Confirms Breach of Consulting GitLab Environment, 28,000 Private Repos Exposed
Red Hat confirmed a security incident after a threat actor accessed its self-managed GitLab instance used for consulting engagements, allegedly compromising 28,000 private repositories, including customer engagement reports. The company says core services and software supply chain remain intact, but the breach carries significant supply chain and credential risks for consulting clients. Key Details
- Threat actor group “Crimson Collective” claims exfiltration of 28,000 private repos and CERs.
- CERs may include network diagrams, configurations, authentication tokens, and customer audit data.
- Red Hat revoked access, isolated the instance, and implemented additional hardening measures.
Read more at Dark Reading, Centre for Cybersecurity Belgium
6. UK Government Guarantees £1.5 B Loan to Stabilize JLR Supply Chain
The UK is underwriting up to £1.5 billion of a commercial loan to Jaguar Land Rover under its Export Development Guarantee program, to restore its supply chain after a catastrophic cyberattack forced the automaker to halt production. This allows the company to secure a significantly larger loan, typically at better terms, than it could obtain on its own after a significant event like JLR is currently dealing with.
Key Details
- JLR employs 34,000 directly and underpins around 120,000 supply-chain roles
- Company lacked finalized cyber insurance when the attack occurred
Next Steps
- Reassess and secure comprehensive cyber insurance coverage
- Monitor supplier financial health and reinforce critical partners
Read more at Bleeping Computer
7. Japanese Beer Giant Asahi Cyberattack Idles 30 Factories, Delays 12 New Products
A cyberattack has crippled Asahi’s Japanese operations since Monday, forcing shutdowns of order processing, shipping and call centers and leaving most of its 30 domestic factories idle. The incident has also pushed back the mid-October launch of a dozen new beverages and consumer goods, raising risks of supply shortages and revenue loss for Japan’s leading brewer.
Key Details
- Shutdown affects order processing, logistics and call centers nationwide
- Twelve product launches, including soft drinks and cough drops, are postponed
- No confirmed customer data leaks; police notified of potential ransomware
- Shares fell 2.6% as outage entered a fourth day
Next Steps
- Review ransomware incident response playbook
- Validate network segmentation and backup integrity
Read more at The Record, Financial Times, TBS News, Asahi Statement, Nikkei
8. CometJacking Prompt Injection Enables One-Click Data Exfiltration via Comet AI Browser
LayerX researchers have revealed “CometJacking,” a prompt-injection attack that hijacks Perplexity’s Comet AI browser via a single malicious URL click, instructing the agent to pull Gmail, Calendar, and other connected data and exfiltrate it using Base64 encoding. This exploit bypasses Comet’s memory-separation safeguards without stealing credentials.
Key Details
- Attack leverages the URL’s “collection” parameter to force memory access
- Base64 encoding masks exfiltrated data to evade Comet’s export checks
- No credentials are stolen, the browser’s existing service tokens are abused
- LayerX disclosed the flaw on August 27; Perplexity deemed it “no security impact”
Next Steps
- Review use of the Comet Browser
Read more at The Hacker News, LayerX Security
Subscribe
Subscribe to receive weekly cybersecurity news summary to your inbox every Monday.